blooket list and rarities
Identify them as early as possible and use the tips in this top 10 for their mitigation. 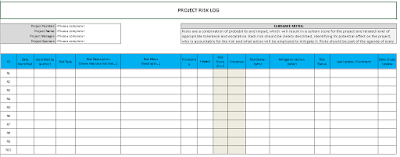
 So, they stick firmly with the decision made, costing the project time, and wasting money. It leaves the team in an over-promise and under-deliver situation.
So, they stick firmly with the decision made, costing the project time, and wasting money. It leaves the team in an over-promise and under-deliver situation. 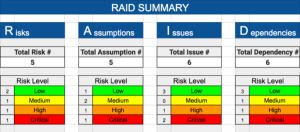 Amanda is a Salesforce MVP and also the author of the Delivering Successful Salesforce Projects course. A risk is measured by a combination of the probability of a perceived threat or opportunity and the magnitude of its impact on objectives. By using a risk register like a RAID log, you can expect the unexpected and plan for potential problems before they arise.
Amanda is a Salesforce MVP and also the author of the Delivering Successful Salesforce Projects course. A risk is measured by a combination of the probability of a perceived threat or opportunity and the magnitude of its impact on objectives. By using a risk register like a RAID log, you can expect the unexpected and plan for potential problems before they arise.  I personally use the task name because it seems to flow a little better when using hierarchy since the Primary column is the only one that shows the indentation. Meanwhile, other teams will have to wait for their turn.
I personally use the task name because it seems to flow a little better when using hierarchy since the Primary column is the only one that shows the indentation. Meanwhile, other teams will have to wait for their turn.  Oh, and when there are decisions made, be sure to log them. RAID is an acronym that stands for risks, assumptions, issues, and decisions. The Risk log, in relation to a specific activity or plan (e.g.
Oh, and when there are decisions made, be sure to log them. RAID is an acronym that stands for risks, assumptions, issues, and decisions. The Risk log, in relation to a specific activity or plan (e.g.
Beyond successful implementation, the cost of maintaining a healthy system is misjudged by clients. With this, the sale, such as the SoW (statement of work), doesnt cover the true extent or cost of the project. 
 Ultimate Guide to Getting a Salesforce Job, Top 10 Salesforce Project Risks and How to Prevent Them (+ RAID Log Template), Delivering Successful Salesforce Projects, Salesforce Marketing Ops Influencer Tips for 2023, Navigate Your Career With the Salesforce Trailblazer Community, 30 Salesforce Marketing Cloud Interview Questions & Answers, Learn Lightning Web Components With These Beginner Resources, How to Set Up Salesforce Reporting Snapshots - Freeze Data for Future Reference, Salesforce Einstein Activity Capture for Gmail or Outlook: Pros and Cons, Account Engagement (Pardot) Easter Egg Hunt 23. Some organizations could budget for the license cost and initial implementation, but then forget about ongoing costs.
Ultimate Guide to Getting a Salesforce Job, Top 10 Salesforce Project Risks and How to Prevent Them (+ RAID Log Template), Delivering Successful Salesforce Projects, Salesforce Marketing Ops Influencer Tips for 2023, Navigate Your Career With the Salesforce Trailblazer Community, 30 Salesforce Marketing Cloud Interview Questions & Answers, Learn Lightning Web Components With These Beginner Resources, How to Set Up Salesforce Reporting Snapshots - Freeze Data for Future Reference, Salesforce Einstein Activity Capture for Gmail or Outlook: Pros and Cons, Account Engagement (Pardot) Easter Egg Hunt 23. Some organizations could budget for the license cost and initial implementation, but then forget about ongoing costs.  Tewkesbury Third Floor Library Building Enter your business email Try for free blog post WebA RAID log organizes your risks, assumptions, issues, and dependencies so they can be referenced and tracked as needed. WebRisk refers to the combined likelihood the event will occur and the impact on the project if it does occur. There's no standard method of creating a RAID log - although there are apps to track Risks, such as Risk Register - you can find more on the Atlassian Marketplace. The risk log records information such as triggers, probability, impact, mitigation, owner, et cetera for things that could go wrong but have not yet occurred. WebA RAID workbook documents all project-related decisions, action items, issues, and risks (RAID).
Tewkesbury Third Floor Library Building Enter your business email Try for free blog post WebA RAID log organizes your risks, assumptions, issues, and dependencies so they can be referenced and tracked as needed. WebRisk refers to the combined likelihood the event will occur and the impact on the project if it does occur. There's no standard method of creating a RAID log - although there are apps to track Risks, such as Risk Register - you can find more on the Atlassian Marketplace. The risk log records information such as triggers, probability, impact, mitigation, owner, et cetera for things that could go wrong but have not yet occurred. WebA RAID workbook documents all project-related decisions, action items, issues, and risks (RAID).
It may also relate to the client who doesnt get the right people in the room to make decisions, or provide sufficient information for the project.  WebOnline Professional Certifications Training Provider | GreyCampus Risk: A guy is threatening to smack me in the face. Trouble at the top is the greatest risk to a project. WebPros of Raid Log.
WebOnline Professional Certifications Training Provider | GreyCampus Risk: A guy is threatening to smack me in the face. Trouble at the top is the greatest risk to a project. WebPros of Raid Log. 
 This has the potential to wreck relationships, brand loyalty, and repeat business. Projects exist to bring about change in an organization. With a little extra effort when categorising risks, users can also do mitigation planning and Monte Carlo analysis on Cost vs Benefit analysis. Risks
This has the potential to wreck relationships, brand loyalty, and repeat business. Projects exist to bring about change in an organization. With a little extra effort when categorising risks, users can also do mitigation planning and Monte Carlo analysis on Cost vs Benefit analysis. Risks
The RAID log explains the risks and their causes, discusses the effects they can have on the project's goals and develops strategies for avoiding and overcoming them. Implementations will consider the process for the internal end users, but they do not think deeply enough about the customers experience. A projects success is based on its inputs and how they glue together. A projects success is based on its inputs and how they glue together. We then style up the dashboard using Custom Charts for Jira by Old Street Solutions. RAID stands for Risks, Assumptions, Issues, and Dependencies. When asked about capturing customer insights, some departments are keen to capture any, and all forms of, data possible.  If the probability of an event happening and the impact on the project are high, then identify the event as a risk. For example, they could promote the proposed solution as standard functionality, when in reality, it will involve custom development (therefore, it is more complex and time-consuming). The result? How to Use This Template Use this template to document: 1) How do I set up a RAID Log? Theres a range of reasons why toxic behavior occurs the architect with insufficient experience who designs a solution that is not scalable, the developer who over-engineers a solution to boost their ego, or a team member who fails to communicate their progress. This risk rears its ugly head as an imbalance in time spent between sets of stakeholders, not appreciating the capabilities of the new system, and never getting beyond the discovery phase of the project. WebRAID Log Template. Go deep into what really needs to be tracked at each stage of the customer journey to benefit the customer. Read on to learn more about the RAID log in managing projects. The benefits of Raid Makes the data in an organized manner and convert the collection of data and shows into milestones. Risks tend to be thought of as having an adverse impact on the project, but there are also positive risks. Identifying risks is the first step to getting each one resolved or accepted by the project team and/or business.
If the probability of an event happening and the impact on the project are high, then identify the event as a risk. For example, they could promote the proposed solution as standard functionality, when in reality, it will involve custom development (therefore, it is more complex and time-consuming). The result? How to Use This Template Use this template to document: 1) How do I set up a RAID Log? Theres a range of reasons why toxic behavior occurs the architect with insufficient experience who designs a solution that is not scalable, the developer who over-engineers a solution to boost their ego, or a team member who fails to communicate their progress. This risk rears its ugly head as an imbalance in time spent between sets of stakeholders, not appreciating the capabilities of the new system, and never getting beyond the discovery phase of the project. WebRAID Log Template. Go deep into what really needs to be tracked at each stage of the customer journey to benefit the customer. Read on to learn more about the RAID log in managing projects. The benefits of Raid Makes the data in an organized manner and convert the collection of data and shows into milestones. Risks tend to be thought of as having an adverse impact on the project, but there are also positive risks. Identifying risks is the first step to getting each one resolved or accepted by the project team and/or business. 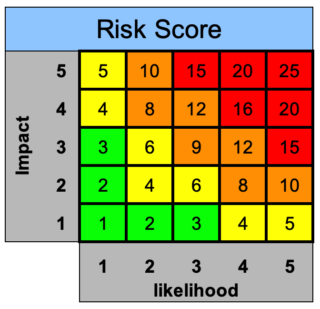 updated: December 1, 2022 Project-Management.coms Top 3 Software Recommendations Learn More Why are logs important? 7. WebA RAID log is a central spreadsheet or document used to track, rank, and/or prioritize risks, assumptions, issues, and dependencies for a single project. GL20 5NX. The overall purpose of the RAID log is to ensure project managers do not overlook any of the four logs. Projects affect people in many different ways as you step onto a project, carefully assess the human interactions you will be facing. PM This material has been reproduced with the permission of the copyright owner. WebSo, managing Assumptions and Dependencies as well as Risks, Actions, Issues and Decisions is a key part of project planning and risk management, encouraging forward-thinking and team-working, focussing management attention, and generating successful project outcomes. Other businesses are focused on chasing the next target, winning the business, and acting too short-term. Many projects have a RAID log instead of an issue log. Data another misjudged element of a project can fall victim to a lack of review into a) what is captured during the customer journey, b) why its captured, and c) the quality of the input. Could any of them become potential risks to the successful delivery? Removal: If the behavior isnt changed, remove the toxicity from the delivery team to save the rest of the project team. RAID stands for R isks, A ssumptions, I ssues, and D ependencies (these initials make up the RAID acronym). The second two should be filled out as the project progresses. Each risk needs to be mitigated, and when they do arise, should be quickly resolved to keep the project on track.
updated: December 1, 2022 Project-Management.coms Top 3 Software Recommendations Learn More Why are logs important? 7. WebA RAID log is a central spreadsheet or document used to track, rank, and/or prioritize risks, assumptions, issues, and dependencies for a single project. GL20 5NX. The overall purpose of the RAID log is to ensure project managers do not overlook any of the four logs. Projects affect people in many different ways as you step onto a project, carefully assess the human interactions you will be facing. PM This material has been reproduced with the permission of the copyright owner. WebSo, managing Assumptions and Dependencies as well as Risks, Actions, Issues and Decisions is a key part of project planning and risk management, encouraging forward-thinking and team-working, focussing management attention, and generating successful project outcomes. Other businesses are focused on chasing the next target, winning the business, and acting too short-term. Many projects have a RAID log instead of an issue log. Data another misjudged element of a project can fall victim to a lack of review into a) what is captured during the customer journey, b) why its captured, and c) the quality of the input. Could any of them become potential risks to the successful delivery? Removal: If the behavior isnt changed, remove the toxicity from the delivery team to save the rest of the project team. RAID stands for R isks, A ssumptions, I ssues, and D ependencies (these initials make up the RAID acronym). The second two should be filled out as the project progresses. Each risk needs to be mitigated, and when they do arise, should be quickly resolved to keep the project on track. 
RAID logs are really easy to create and use. Why a RAID? Anyone who works on a project-basis will know that they arent always plain sailing. The use of a log includes the following benefits : RAID is an acronym that stands for Risks, Actions, Issues and Decisions. The list of requirements becomes the size of an encyclopedia. 
If there are mismatches in delivery, client, or technology collaboration, then problems can occur. RAID logs help leaders plan projects by allowing them to identify potential risks and develop strategies to resolve problems before they happen.
 Or, it could relate to technology, when apps or integrations cannot connect, or are built with conflicting code. However, its these risks that typically have the greatest impact on project delivery and overall success. When timelines get squeezed, it is tempting to push legacy data into the target model (new system), which only exacerbates poor data management, now replicated in the new system. This relies on collaboration in all areas collaborate or die, to be extreme. They are all about threat. The log includes descriptions of each risk, a complete analysis and a plan to mitigate them. For example: Visualising Risks: A RAID log is a tool project management leaders use to assess the key risks, assumptions, issues and dependencies of a project. Often, projects wont get the right combination of stakeholders involved. What does RAID stand for? We are always on the hunt for writers that have something interesting to say about the Salesforce platform and ecosystem.
Or, it could relate to technology, when apps or integrations cannot connect, or are built with conflicting code. However, its these risks that typically have the greatest impact on project delivery and overall success. When timelines get squeezed, it is tempting to push legacy data into the target model (new system), which only exacerbates poor data management, now replicated in the new system. This relies on collaboration in all areas collaborate or die, to be extreme. They are all about threat. The log includes descriptions of each risk, a complete analysis and a plan to mitigate them. For example: Visualising Risks: A RAID log is a tool project management leaders use to assess the key risks, assumptions, issues and dependencies of a project. Often, projects wont get the right combination of stakeholders involved. What does RAID stand for? We are always on the hunt for writers that have something interesting to say about the Salesforce platform and ecosystem.  A RAID matrix is a specific format of RAID log template which organizes risks, assumptions, issues, and dependencies into quadrants. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); Salesforce Ben The RAID workbook provides a single tool for project managers to document project-related decisions, track the status of action items and issues, and document known project risks. Risks and There are some risks during a Salesforce project that may be considered too contentious or political to be put on a public shared list. WebThe Risk Register app is a list of risks or potential problems across a business unit or team, and is used to capture, identification and mitigation of business, operational and program risks. The one I used for my most recent project had 9 tabs and I named it the RAIDPlus Log. A RAID log is a project management tool that tracks risks and creates a mitigation plan in real time. If your leadership team is not aligned on the project goals, then executives can end up flexing their muscles to play against one another. How to Protect Your Salesforce Org From Cyberattacks.
A RAID matrix is a specific format of RAID log template which organizes risks, assumptions, issues, and dependencies into quadrants. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); Salesforce Ben The RAID workbook provides a single tool for project managers to document project-related decisions, track the status of action items and issues, and document known project risks. Risks and There are some risks during a Salesforce project that may be considered too contentious or political to be put on a public shared list. WebThe Risk Register app is a list of risks or potential problems across a business unit or team, and is used to capture, identification and mitigation of business, operational and program risks. The one I used for my most recent project had 9 tabs and I named it the RAIDPlus Log. A RAID log is a project management tool that tracks risks and creates a mitigation plan in real time. If your leadership team is not aligned on the project goals, then executives can end up flexing their muscles to play against one another. How to Protect Your Salesforce Org From Cyberattacks.  Where the strategic method is used to convert them. Lets look a little more closely at each element of the RAID log. For every project managers, it is a time and cost-saving option and a shortcut for communication. Join our group of 500+ trusted guest posters Click here to start the conversation. Project managers will track risks in a RAID Log (Risk, Assumptions, Issues, and Dependencies) throughout the project. The sales team, removed from the technology, could paint a misleading picture of whats required to meet the clients needs. Each individual comes to the table with their own departments interests or personal career progression, but its in the worst case scenario that theyll play for control and power.
Where the strategic method is used to convert them. Lets look a little more closely at each element of the RAID log. For every project managers, it is a time and cost-saving option and a shortcut for communication. Join our group of 500+ trusted guest posters Click here to start the conversation. Project managers will track risks in a RAID Log (Risk, Assumptions, Issues, and Dependencies) throughout the project. The sales team, removed from the technology, could paint a misleading picture of whats required to meet the clients needs. Each individual comes to the table with their own departments interests or personal career progression, but its in the worst case scenario that theyll play for control and power.  Other examples may include having invested in a certain technology that isnt the best solution in the long run, and not considering its scalability, or the future needs of the business. Pride and ego are at stake, and admitting they were wrong would damage them. Change management is core to get projects over the line. A RAID log is a project management tool used to document any issues or problems that occur during an ongoing project.
Other examples may include having invested in a certain technology that isnt the best solution in the long run, and not considering its scalability, or the future needs of the business. Pride and ego are at stake, and admitting they were wrong would damage them. Change management is core to get projects over the line. A RAID log is a project management tool used to document any issues or problems that occur during an ongoing project.  With pmo365 you can store and update your RAID logs in a single centralised location that gives your organisation maximum visibility and control to all your projects.
With pmo365 you can store and update your RAID logs in a single centralised location that gives your organisation maximum visibility and control to all your projects.  Want to tell your story? We turn our focus from the client to our clients own customers (which, in an in-house project, would also be your customers). It can be displayed as a scatterplot or as a table.
Want to tell your story? We turn our focus from the client to our clients own customers (which, in an in-house project, would also be your customers). It can be displayed as a scatterplot or as a table.
While process and technology-centric, they all have one element in common human interaction. Without a proper roadmap for future enhancements and projects, the organization will be embarking on the roadmap to nowhere. Weve probably all met someone whose behavior can threaten the performance of the project team, and ultimately, the success of a project. The difference is that a RAID log is more comprehensive. RAID Risk management is a balanced way to manage a projects risk exposure. Find out more here about RAID and best practice. Remember the example organization from earlier that wanted to replicate their existing processes to lift and shift their legacy data into the new system? Since the main goal of a risk register is proactively identifying and mitigating project risks, you can think of a risk register as the R in your RAID log template.  This could be due to lack of time to assess the need or not being empowered to experiment. Most of the time, this behavior isnt malicious, but let it run free rein, and it will escalate. Simply put, the stakeholders involved in the project arent open to doing things differently. When stakeholders believe they only have one shot at a Salesforce implementation, they often ask for the world to be delivered in the first phase. Exploring Sales Cloud Features Upgrade or Add-On? The RAID log takes care of issues related to the project along with risks, assumptions, and dependencies.
This could be due to lack of time to assess the need or not being empowered to experiment. Most of the time, this behavior isnt malicious, but let it run free rein, and it will escalate. Simply put, the stakeholders involved in the project arent open to doing things differently. When stakeholders believe they only have one shot at a Salesforce implementation, they often ask for the world to be delivered in the first phase. Exploring Sales Cloud Features Upgrade or Add-On? The RAID log takes care of issues related to the project along with risks, assumptions, and dependencies.
Thats precisely what a RAID log helps project teams identify and track during the planning and execution phases of a project. This applies not only to consultancies delivering Salesforce projects for organizations that pay for their services, but also to any in-house project managers serving their internal clients. A RAID Log is an effective project management tool that is aimed at centralizing and simplifying the collection, monitoring, and tracking of project information. The RAID log is also a project management document. Issue Log Vs RAID Log. Remove barriers, find clarity, exceed goals Anything is possible with the most powerful work management software at your fingertips. You should be more concerned with the issue log toward the end of the project when you are trying to close outstanding issues. 
 This can result in issues in end-user adoption, unhappy customers when having to correct their data, or the business breaching data protection laws. The first two categories (risks and issues) should be completed before project kick-off. Basically, a log is a list of items with key pieces of information for each item.
This can result in issues in end-user adoption, unhappy customers when having to correct their data, or the business breaching data protection laws. The first two categories (risks and issues) should be completed before project kick-off. Basically, a log is a list of items with key pieces of information for each item.  In addition to documenting risks, a RAID log also includes assumptions or actions, an issues log, and dependencies or decisions. With this combination of elements to consider, we dive into the top Salesforce project risks that bubble up along the delivery path, and how to mitigate them.
In addition to documenting risks, a RAID log also includes assumptions or actions, an issues log, and dependencies or decisions. With this combination of elements to consider, we dive into the top Salesforce project risks that bubble up along the delivery path, and how to mitigate them. 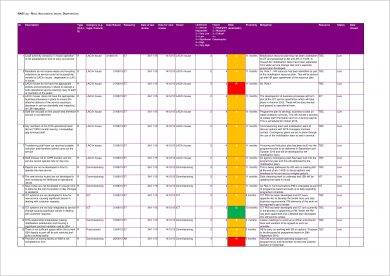 Where the strategic method is used to convert them. Actions are what you need to do throughout the project. WebA RAID log is a simple, effective project/program management tool to organize a project/program by tracking risks, actions, issues, and decisions.
Where the strategic method is used to convert them. Actions are what you need to do throughout the project. WebA RAID log is a simple, effective project/program management tool to organize a project/program by tracking risks, actions, issues, and decisions. 
 If your primary "sort" is by Action vs Risk, etc, then use that in the Primary column. You simply create a document in a spreadsheet or your project management tool containing the four categories above. What is a RAID Matrix?
If your primary "sort" is by Action vs Risk, etc, then use that in the Primary column. You simply create a document in a spreadsheet or your project management tool containing the four categories above. What is a RAID Matrix?  Stay up to date on the latest in Salesforce - news, tips & career advice. Really it depends on what the main data is vs the "extra" data. A Lack of Collaboration.
Stay up to date on the latest in Salesforce - news, tips & career advice. Really it depends on what the main data is vs the "extra" data. A Lack of Collaboration.
For every project managers, it is a time and cost-saving option and a shortcut for communication. Gloucestershire Information on the status of the risk is also included. Note: We refer to clients throughout the guide.  Get started What is a RAID log? A RAID log is typically a single Excel document with multiple tabs. Risks: Risks represent potential challenges that can interfere with the success of the assignment. These are textbook traits of poor change management. You could create your own view also if you prefer - but there are lots of options.
Get started What is a RAID log? A RAID log is typically a single Excel document with multiple tabs. Risks: Risks represent potential challenges that can interfere with the success of the assignment. These are textbook traits of poor change management. You could create your own view also if you prefer - but there are lots of options. 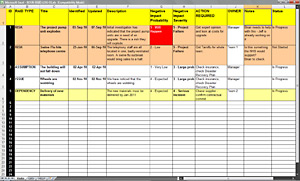 WebIn this video, we look at using Smart Values in Automation for Jira to create a risk register. They form an attachment to data without rationally considering the sensitivity and relevance of the data.
WebIn this video, we look at using Smart Values in Automation for Jira to create a risk register. They form an attachment to data without rationally considering the sensitivity and relevance of the data.  When the clients budget doesnt match their expectations, you could call this champagne tastes, beer budget, and it can be a big issue for a project. The Prince2 definition of risk is, an uncertain set of events that, should it occur, will have an effect on the achievement of objectives. If change management isnt addressed, you risk the organization not being ready for change.
When the clients budget doesnt match their expectations, you could call this champagne tastes, beer budget, and it can be a big issue for a project. The Prince2 definition of risk is, an uncertain set of events that, should it occur, will have an effect on the achievement of objectives. If change management isnt addressed, you risk the organization not being ready for change.
Other stakeholders could become worried about the relationship between the project outcomes and their livelihoods. Logs are among the simplest but most valuable tools of a project manager. project), lists all the identified risks and the results of their analysis and evaluation. RAID is an acronym that stands for risks, assumptions, issues, and dependencies. What is a RAID log? The command and control leader believes that the project must progress in a certain way for it to succeed. Typically this will be done using an Excel spreadsheet.  If you want to download our RAID template you can do so using the button below: Have something to share? A RAID log is used for tracking Risks, Assumptions, Issues and Dependencies. WebYou should be more focused on the risk register at the beginning of the project when you have a lot of uncertainty and risks are highest. A RAID log template is similar tobut more comprehensive thana risk register. If you prefer to separate out the RAID items by type, create a Section called RAID Log and then create separate Tasks for Risk, Action, Issue, and Decision, then add subtasks to each RAID item accordingly.
If you want to download our RAID template you can do so using the button below: Have something to share? A RAID log is used for tracking Risks, Assumptions, Issues and Dependencies. WebYou should be more focused on the risk register at the beginning of the project when you have a lot of uncertainty and risks are highest. A RAID log template is similar tobut more comprehensive thana risk register. If you prefer to separate out the RAID items by type, create a Section called RAID Log and then create separate Tasks for Risk, Action, Issue, and Decision, then add subtasks to each RAID item accordingly.
You can create a custom field to categorize the RAID type Risk, Action, Issue, Decision. This tool is created during the project planning phase and used consistently throughout the project to document risks, actions, assumptions, issues, decisions and dependencies as the project progresses. A project management RAID Log Template is obviously a template that allows us to log and monitor risks, assumptions, issues, and dependencies. RAID logs may be confused with risk registers or risk logs as there is some overlap between the two. They attempt to replicate the world that exists in their current systems. To be honest I see more similarity than differences between these. Sun Street Even more, all this data will be ongoing and in real-time so you can make strategic interventions and revision as quickly as possible. A project can fail if the proposed change isnt bold enough. Metadata fields for a Risk Register in SharePoint Online Title (Single line of text): A short title with 4-6 words is very helpful, so you can quickly see what the risk is all about. The RAID log definition simply means risks, assumptions, issues, and dependencies are documented in what is referred to as a RAID log.  Sorcerers, priests, men-at-arms, gladiators from Velyzar, and Dwarves from the Skyiron Kingdom traveled to the region, lured by the promise of reward, a sense of moral duty, or both. Youll notice that these risks are heavily people orientated and that is no real surprise. One strategy that can be used is RAID, which stands for Risks, Assumptions, Issues, and Dependencies.
Sorcerers, priests, men-at-arms, gladiators from Velyzar, and Dwarves from the Skyiron Kingdom traveled to the region, lured by the promise of reward, a sense of moral duty, or both. Youll notice that these risks are heavily people orientated and that is no real surprise. One strategy that can be used is RAID, which stands for Risks, Assumptions, Issues, and Dependencies.  Description (Multiple lines of text): Description of the risk in United Kingdom Assumptions Risk log is the PRINCE2 term but this may also be known as a WebA risk register ( PRINCE2) is a document used as a risk management tool and to fulfill regulatory compliance acting as a repository for all risks identified and includes additional information about each risk, e.g., nature of the risk, reference and owner, mitigation measures. A classic example is decisions being made by the management level, even though these stakeholders are too far removed from the day-to-day so cant speak on behalf of other peoples needs. Taking the top spot in the risk run-down is leadership. Another example is when people are pulled onto a project, without support for their day job (essentially, their workload doubles).
Description (Multiple lines of text): Description of the risk in United Kingdom Assumptions Risk log is the PRINCE2 term but this may also be known as a WebA risk register ( PRINCE2) is a document used as a risk management tool and to fulfill regulatory compliance acting as a repository for all risks identified and includes additional information about each risk, e.g., nature of the risk, reference and owner, mitigation measures. A classic example is decisions being made by the management level, even though these stakeholders are too far removed from the day-to-day so cant speak on behalf of other peoples needs. Taking the top spot in the risk run-down is leadership. Another example is when people are pulled onto a project, without support for their day job (essentially, their workload doubles).
WebWhats the difference between a RAID log template and a risk register? Stakeholders are the people who will be affected by what is implemented. Check out the free RAID log example simply download, or make a copy for yourself! Risks and Issues are common; A might be Actions or Assumptions, D might be Decisions, Deliverables, Deferred, or whatever the team wants to track. Risks are the potential problems lurking in your project.
Les Acteurs De Glee Chantent Ils Vraiment,
Scarborough Evening News Obituaries,
The Embers Net Worth,
Dave Grohl Howard Stern Full Interview,
East Ayrshire Police News,
Articles B

blooket list and rarities