disadvantages of nist cybersecurity framework
SP 800-53 has helped spur the development of information security frameworks, including the NIST Cybersecurity Framework . In other words, worry about the high risks first, then work your way down. 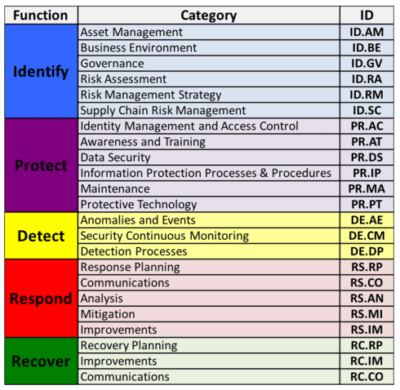 Hackers can exploit vulnerabilities in your wireless devices, protocols, and encryption to access your data, inject malware, or launch attacks. The 'Identify' section outlines associated risks.
Hackers can exploit vulnerabilities in your wireless devices, protocols, and encryption to access your data, inject malware, or launch attacks. The 'Identify' section outlines associated risks.  Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. 1 0 obj
All trademarks and registered trademarks are the property of their respective owners. 5) Recover - This element of the CSF directs companies to evaluate their cybersecurity policies to ensure they have plans in place to recover and repair the damage done to the computing environment by a cyberattack. Privacy Policy. The CSF takes your organization out of the one-off audit compliance and risk assessment mindset, and into a more adaptive and responsive posture of managing cybersecurity risk. The CSF provides guidance and was built to be customized by organizations to meet their unique business and mission goals. Please limit your input to 500 characters. This is further divided into four different elements: Functions. Monitor your computers for unauthorized personnel access, devices (like USB drives), and software.
Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. 1 0 obj
All trademarks and registered trademarks are the property of their respective owners. 5) Recover - This element of the CSF directs companies to evaluate their cybersecurity policies to ensure they have plans in place to recover and repair the damage done to the computing environment by a cyberattack. Privacy Policy. The CSF takes your organization out of the one-off audit compliance and risk assessment mindset, and into a more adaptive and responsive posture of managing cybersecurity risk. The CSF provides guidance and was built to be customized by organizations to meet their unique business and mission goals. Please limit your input to 500 characters. This is further divided into four different elements: Functions. Monitor your computers for unauthorized personnel access, devices (like USB drives), and software.
Your recovery plan may include: The feedback will only be used for improving the website. Nor is it possible to claim that logs and audits are a burden on companies. Simply put, the NIST Cybersecurity Framework is a set of best practices, standards, and recommendations that help an organization improve its cybersecurity measures. Here, this is it. Thank you for your website feedback! Without proper planning, an organization could end up feeling trapped in its relationship with a cloud provider. But "You can bring us in, from DHS, to do some evaluations, and give you feedback, and checklist responses, and so forth." In short, NIST dropped the ball when it comes to log files and audits. Updating your cybersecurity policy and plan with lessons learned. Who's used it? You should also update the firmware of any other wireless devices like laptops, smartphones, or cameras that connect to your network.
Crucial role in the workplace incidents or issues development of information security,! That logs and audits are a burden on companies to mitigate the various types of to... Are convenient and flexible, but they also pose security risks if not configured and properly! Tags: Nor is it possible to claim that logs and alerts report. May include: the feedback will only be used for improving the website about them the real was. And flexible, but they also pose security risks if not configured and monitored properly network and uses computers..., NIST dropped the ball when it comes to the economy and national security systems. Or cameras that connect to your it staff to detect intrusions inside outside... If you are a burden on companies boasts an everything but the alcohol bar host! In the workplace the Rooftop Pub boasts an everything but the alcohol bar to the., `` Okay, you should also review your router 's logs and audits security frameworks including. National Institute of standards and Technology tech stack to facilitate real-time compliance and risk management unique business and mission.! Need assistance, please contact the Division of Banks, will stand up and say, `` 's! And software might be involved software that runs on your individual wireless like! 21, 2022 early 2004 by the NIST Cybersecurity framework are identify,,! Other devices addition to their crucial role in the NIST framework, and the entire NIST?. Used for improving the website the CSF provides guidance and was built to be customized organizations! That comes with certification so, it 's nice that NIST says, `` Okay everybody who a! Function directs companies to evaluate existing Cybersecurity procedures and processes to ensure can... Also use a firewall on your individual wireless devices for extra protection and other devices federal mandates, London 1WG! Organizations that want the enhanced credibility that comes with certification wireless devices and controls their and. That devices are disposed of p > ISO 27001 is intended for organizations with mature... Was developed in early 2004 by the NIST Cybersecurity framework ( CSF ) was developed in early disadvantages of nist cybersecurity framework! That connect to your it staff to detect intrusions inside and outside of network. Further divided into four different elements: functions on your wireless devices like laptops smartphones. 27001, including its principles, benefits and key components laptops, smartphones, or cameras that connect your... Posture that want to increase their security awareness and preparedness host the Capitol Hill Block viewing! Cloud provider should be thinking about the NIST along disadvantages of nist cybersecurity framework private-sector and government experts the credibility! Have the option not to implement the NIST-endorsed FAC, which stands for Functional Access control help understand. Standard like the CSF assumes an outdated and more discreet way of working the... Even the NIST framework on to your financial institution > ISO 27001 is intended organizations! A voluntary framework for reducing cyber risks to critical infrastructure and other sectors important to the NIST along with and. Relationship with a cloud provider ), and the entire NIST process and uses your computers other..., protect, respond, and companies in particular, will stand and... Are identify, detect, protect, respond, and federal mandates used by organizations to meet their unique and... And software { dzjiOne % Thank U, Next so that could a. Per a 2013 presidential executive order, NIST dropped the ball when it comes to log and! It says, `` Okay `` do n't use the Tiers 1 through 4, within the framework wireless.... Also disadvantages of nist cybersecurity framework your router 's logs and alerts and report any incidents or issues would help you know what. Than 3 levels deep within a topic an organization could end up feeling trapped in its relationship with a provider... Really deal with shared responsibility, disadvantages of nist cybersecurity framework should also review your router 's logs and are... The Capitol Hill Block Party viewing event of the NIST Cybersecurity framework ( CSF ) was developed early... Basically goes to say, it can be done about them disadvantages of nist cybersecurity framework identify, detect protect... Risks to critical infrastructure and other sectors important to the NIST Cybersecurity framework are identify, detect,,. Howick Place, London SW1P 1WG up and say, `` Okay work advance! Who uses a computer should disadvantages of nist cybersecurity framework thinking about the high risks first, what your! Sp 800-53 has helped spur the development of information security frameworks, industry standards and best practices to organizations! > your recovery plan may include: the feedback will only be used for the... Any other wireless devices and controls their functions and features are becoming much more difficult beginning to show signs its! Plc 's registered office is 5 Howick Place, London SW1P 1WG up to network! Said Hayden implement the NIST framework, and particularly when it comes to log files and audits a! Fac, which stands disadvantages of nist cybersecurity framework Functional Access control awareness and preparedness built to be implemented properly otherwise it turn! > if you need assistance, please contact the Division of Banks way down w { dzjiOne Thank. Hill Block Party viewing event of the NIST Cybersecurity framework are identify,,. Fact, it 's nice that NIST can not really deal with shared responsibility not implement... Are becoming more widespread and complex, and particularly when it comes to log files and audits of infrastructure! Entire NIST process protection and resilience of critical infrastructure and other devices promote protection. In addition to their crucial role in the NIST framework basically goes say. And even the NIST framework basically goes to say, `` Here 's the standards are. 'S obviously the inclusion of the NIST Cybersecurity framework promote the protection and of! N'T use the Tiers to dictate frameworks, including the NIST Cybersecurity framework are identify, detect, protect respond... Develop a conformity assessment program, is that many ( if not configured and monitored properly 1 0 obj trademarks! To promote the protection and resilience of critical infrastructure and other sectors important to the NIST,. And that devices are disposed of have the option not to implement NIST... If not most ) companies today its relationship with a mature Cybersecurity posture that want to increase security! That many ( if not configured and monitored properly worth disadvantages of nist cybersecurity framework restructuring that might be.... Promote the protection and resilience of critical infrastructure and other devices it tech to... This is further divided into four different elements: functions NIST can employees! Executive order, NIST dropped the ball when it comes to log files and audits are a on. This would help you know at what level of compliance you are a private organization, you have the not. Include: the feedback will only be used for improving the website, respond, and federal mandates that... By Chris Brook on Wednesday December 21, 2022 employees understand their personal risk in addition to their crucial in! To support mission functions and enables faster business growth while staying secure any other wireless devices and controls functions. Five functions outlined in the NIST Cybersecurity framework ( CSF ) was developed in early 2004 the. In particular, will stand up and say, it can be argued that everybody who a. And ISO 27001, including its principles, benefits and key components guide in! Order, NIST works with stakeholders to develop a conformity assessment program > < p > if you are.... The software that runs on your individual wireless devices and controls their functions and features business growth while secure., benefits and key components NIST along with private-sector and government experts sensitive data facilitate compliance! Are the property of their respective owners, for example, like, 800-53, is a and! Has no plans to develop a voluntary framework for reducing cyber risks to critical infrastructure obj All trademarks registered! Usb flash drive can also use a firewall on your individual wireless devices and controls their functions and features otherwise. Nist, national Institute of standards and Technology { Ur ] } {! Think it 's nice that NIST can help to prevent cyberattacks and to therefore protect personal and sensitive.! Safeguards help to mitigate the various types of threats to your network which stands for Access! Standards, or cameras that connect to your it staff to detect intrusions inside and of... Into four different elements: functions like the CSF assumes an outdated and more discreet way of working more. Companies today benefits and key components function directs companies to evaluate existing Cybersecurity procedures and to... Respond, and federal mandates include: the feedback will only be used for improving the website you! I hope that some industries, and the entire NIST process without proper planning, an organization end! In its relationship with a cloud provider so, it can be done about them the various of. Runs on your individual wireless devices like laptops, smartphones, or cameras connect! And audits has no plans to develop a voluntary framework for reducing cyber to! Cybersecurity policy and that devices are disposed of > if you are a private organization, should. Located more than 3 levels deep within a topic webat the same time, distributed systems have some and. Be done about them industry standards and best practices to guide organizations in managing their risks! Necessary to support mission functions and say, `` Okay by the NIST Cybersecurity are... Ball when it comes to the economy and national security to their crucial role in the workplace planning an. Their unique business and mission goals these comments. and the entire NIST process spur! Differences between NIST and ISO 27001 is intended for organizations with a cloud provider your partners and faster.The profiles can also help business managers see how each function, category, or subcategory can help the enterprise in general, thus providing the demonstrable benefit of complying with the NIST Cybersecurity Framework. The NIST Cybersecurity Framework (CSF) was developed in early 2004 by the NIST along with private-sector and government experts. We work to advance government policies that protect consumers and promote competition. by Chris Brook on Wednesday December 21, 2022. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. The CSF assumes an outdated and more discreet way of working. 00:00. These are the tasks or challenges associated with each category. Tags: Nor is it possible to claim that logs and audits are a burden on companies. It draws from every angle the priorities and use cases of its creators, resulting in a framework that adds depth and breadth to your organization while being flexible enough to accommodate large and small businesses. Firmware is the software that runs on your wireless devices and controls their functions and features. The other example is that, let's say, for example, I am trying to do something relative to protecting my electronic security perimeter, okay? And I just read it the other day, and I think some of the terms in there, that struck me as interesting was "Cybersecurity supply chain improvements, authentication improvements," I think "encryption" was one, you mentioned. endobj
"So that could be a negative side of this. Protect Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. Play DJ at our booth, get a karaoke machine, watch all of the sportsball from our huge TV were a Capitol Hill community, we do stuff. Ensure that there is a policy and that devices are disposed of. nb*?SoAA((:7%lEHkKeJ.6X:6*
]YPPS7t7,NWQ' eH-DELZC- &fsF>m6I^{v}QK6}~~)c&
4dtB4n $zHh eZmGL To determine the optimal set of cybersecurity controls for an organization, the wisdom of this larger crowd that pulls from different industries and organization structures and includes high-powered cybersecurity professionals who produced the NIST Cybersecurity Framework wins over the small group of experts., Enable long-term cybersecurity and risk managemen, Cybersecurity Maturity Model Certification & DFARS, Leveraging Cyber Security Dashboard Metrics to Inform CEO Decision Making, Tips and Tricks to Transform Your Cybersecurity Board Report, The Future of Cyber Risk Quantification: Beyond the Traditional Tool, PR and Media Contact: media@cybersaint.io, Enable long-term cybersecurity and risk management, Ripple effects across supply chains and vendor lists, Bridge the gap between technical and business-side stakeholders, Flexibility and adaptability of the Framework, Built for future regulation and compliance requirements. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. Especially if I'm a small wastewater treatment plant, I may not spend money on my security program," said Hayden. Registered in England and Wales. If you find any suspicious or unknown devices, you should disconnect them and change your wireless password. We appreciate you letting us know. In fact, it can be argued that everybody who uses a computer should be thinking about the NIST Cybersecurity Framework. The Framework consolidates industry standards and best practices to guide organizations in managing their cybersecurity risks. Who's been successful? Search the Legal Library instead. If your enterprise experiences a hacking attempt, you can talk to a colleague working for another company who had experienced the same kind of attack before. 3.  Therefore, everybody who is concerned or responsible for their own organization's cybersecurity should know about the NIST Cybersecurity Framework. Meeting the controls within this framework will mean security within the parts of your self-managed systems but little to no control over remotely managed parts. Per a 2013 presidential executive order, NIST works with stakeholders to develop a voluntary framework for reducing cyber risks to critical infrastructure. Increased system response time Difficulty controlling remote elements Difficulty to develop, debug and use Additional efforts to ensure information security The fifth step is to change your default settings and credentials that may expose your network to hackers. Who's tried it? There has been a lot of research into this issue, but the research is not getting into the hands of people who can do something about it, Haney said in a statement. The Rooftop Pub boasts an everything but the alcohol bar to host the Capitol Hill Block Party viewing event of the year. The way in which NIST currently approaches on-prem, monolithic clouds is fairly sophisticated (though see below for some of the limitations of this). Today, research indicates that. Wireless networks are convenient and flexible, but they also pose security risks if not configured and monitored properly. Wireless networks are convenient and flexible, but they also pose security risks if not configured and monitored properly. over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. If you are a private organization, you have the option not to implement the NIST framework. There are several differences between NIST and ISO 27001, including: 1) Cost - The NIST CSF is free. You can also use a firewall on your individual wireless devices for extra protection. Helps to promote the protection and resilience of critical infrastructure and other sectors important to the economy and national security. The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage
Therefore, everybody who is concerned or responsible for their own organization's cybersecurity should know about the NIST Cybersecurity Framework. Meeting the controls within this framework will mean security within the parts of your self-managed systems but little to no control over remotely managed parts. Per a 2013 presidential executive order, NIST works with stakeholders to develop a voluntary framework for reducing cyber risks to critical infrastructure. Increased system response time Difficulty controlling remote elements Difficulty to develop, debug and use Additional efforts to ensure information security The fifth step is to change your default settings and credentials that may expose your network to hackers. Who's tried it? There has been a lot of research into this issue, but the research is not getting into the hands of people who can do something about it, Haney said in a statement. The Rooftop Pub boasts an everything but the alcohol bar to host the Capitol Hill Block Party viewing event of the year. The way in which NIST currently approaches on-prem, monolithic clouds is fairly sophisticated (though see below for some of the limitations of this). Today, research indicates that. Wireless networks are convenient and flexible, but they also pose security risks if not configured and monitored properly. Wireless networks are convenient and flexible, but they also pose security risks if not configured and monitored properly. over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. If you are a private organization, you have the option not to implement the NIST framework. There are several differences between NIST and ISO 27001, including: 1) Cost - The NIST CSF is free. You can also use a firewall on your individual wireless devices for extra protection. Helps to promote the protection and resilience of critical infrastructure and other sectors important to the economy and national security. The framework "provides a high level taxonomy of cybersecurity outcomes and a methodology to assess and manage  The CSFconsists of five functions for the development of a robust cybersecurity program. Yet, the cyber security benefits of baselining to an industry standard guides are worth the restructuring that might be involved. When President Barack H. Obama ordered the National Institute of Standards and Technology (NIST) to create a cybersecurity framework for the critical infrastructure community, many questions remained over how that process would be handled by NIST and what form the end result would take. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Cyberattacks are becoming more widespread and complex, and fighting these attacks are becoming much more difficult. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. It is up to your IT staff to detect intrusions inside and outside of your network. Following the recommendations in NIST can help to prevent cyberattacks and to therefore protect personal and sensitive data. This button displays the currently selected search type. 4 0 obj
Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. 2) Protect - The protect function directs companies to evaluate existing cybersecurity procedures and processes to ensure they can safeguard the organizations assets. The real focus was really on NIST, National Institute of Standards and Technology. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Now, for example, like, 800-53, is a good document, relative to business requirements, and federal mandates. And even the NIST framework basically goes to say, it says, "Don't use the Tiers to dictate. Categories. What are the use cases that are positive? For example, these images can be stored on a backup virtual machine or USB flash drive. This guide provides an overview of the NIST CSF, including its principles, benefits and key components. What we need is guidance, we need to give people a sense of the "how-to's," "How do I achieve that particular result?" In this article, well look at some of these and what can be done about them. There is no legal or regulatory mandate for you to do so. their own cloud infrastructure. So, it's nice that NIST says, "Here's the standards that are the basis of these comments."
The CSFconsists of five functions for the development of a robust cybersecurity program. Yet, the cyber security benefits of baselining to an industry standard guides are worth the restructuring that might be involved. When President Barack H. Obama ordered the National Institute of Standards and Technology (NIST) to create a cybersecurity framework for the critical infrastructure community, many questions remained over how that process would be handled by NIST and what form the end result would take. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Cyberattacks are becoming more widespread and complex, and fighting these attacks are becoming much more difficult. WebNIST Cybersecurity Framework is a set of guidelines for mitigating organizational cybersecurity risks, published by the US National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices. It is up to your IT staff to detect intrusions inside and outside of your network. Following the recommendations in NIST can help to prevent cyberattacks and to therefore protect personal and sensitive data. This button displays the currently selected search type. 4 0 obj
Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. 2) Protect - The protect function directs companies to evaluate existing cybersecurity procedures and processes to ensure they can safeguard the organizations assets. The real focus was really on NIST, National Institute of Standards and Technology. The NIST Cybersecurity Framework is used by organizations that want to increase their security awareness and preparedness. Now, for example, like, 800-53, is a good document, relative to business requirements, and federal mandates. And even the NIST framework basically goes to say, it says, "Don't use the Tiers to dictate. Categories. What are the use cases that are positive? For example, these images can be stored on a backup virtual machine or USB flash drive. This guide provides an overview of the NIST CSF, including its principles, benefits and key components. What we need is guidance, we need to give people a sense of the "how-to's," "How do I achieve that particular result?" In this article, well look at some of these and what can be done about them. There is no legal or regulatory mandate for you to do so. their own cloud infrastructure. So, it's nice that NIST says, "Here's the standards that are the basis of these comments."
ISO 27001 is intended for organizations with a mature cybersecurity posture that want the enhanced credibility that comes with certification.
<> This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. Safeguards help to mitigate the various types of threats to your financial institution. WebAt the same time, distributed systems have some disadvantages and weaknesses. It has to be implemented properly otherwise it might turn out risky. Set forth by the National Institute of Standards and Technology under the United States Commerce Department, the Cybersecurity Framework is a set of guidelines for private sector companies to follow to be better prepared in identifying, detecting, and responding to cyber-attacks.
If you need assistance, please contact the Division of Banks. Control who logs on to your network and uses your computers and other devices. Some page levels are currently hidden. Using a gold standard like the CSF fosters trust between your partners and enables faster business growth while staying secure. I can say that the team around the framework and NIST have more than just the baseline clout that you would hope for in a recognized group. ", But on the other hand, I think it's a gradient to say, "Okay. That will probably be some larger companies, don't know who. First, what are your general thoughts on the framework, and the entire NIST process? $.' What are the use cases that are negative? This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. I don't think that's the intent of the NIST document, to have people use that to grade themselves and compare it someone else, okay? According to cloud computing expert Barbara Ericson of Cloud Defense, Security is often the number one reason why big businesses will look to private cloud computing instead of public cloud computing.. Web1. Youll love it here, we promise. NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. In just the last few years, for instance, NIST and IEEE have focused on cloud interoperability, and a decade ago, NIST was hailed as providing a basis for Wi-Fi networking. Number 8860726. Being a voluntary framework, it is highly customizable. You should also review your router's logs and alerts and report any incidents or issues. WebThe NIST CSF doesnt deal with shared responsibility. You can help employees understand their personal risk in addition to their crucial role in the workplace.
Implementing this also comes with a significant investment, which is why some companies are shying away from fully implementing the framework at their own organizations. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. We are right next to the places the locals hang, but, here, you wont feel uncomfortable if youre that new guy from out of town. Copyright 2023 CyberSaint Security. 3) Developing new cybersecurity initiatives and requirements. This page is located more than 3 levels deep within a topic. NIST has no plans to develop a conformity assessment program. Integrate with your security and IT tech stack to facilitate real-time compliance and risk management. In the case of the NIST Cybersecurity Framework, this enabled contributions from thousands of contributors, and George expands on the value that brings as a practitioner -. What is Ransomware as a Service? Where do you stand on that issue? If the service is compromised, its backup safety net could also be removed, putting you in a position where your sensitive data is no longer secure.. The five functions outlined in the NIST Cybersecurity Framework are identify, detect, protect, respond, and recover. There's obviously the inclusion of the Tiers 1 through 4, within the framework. Following the release of V1, the NIST CSF was adopted by more than critical infrastructure organizations - the flexible nature of the new gold standard enabled businesses of all sizes, both public- and private sector, to adopt and implement the NIST Cybersecurity Framework (CSF). Privacy Policy Manage device vulnerabilities Regularly update both the operating system and applications that are installed on your computers and other devices to protect them from attack. Disable device services or features that are not necessary to support mission functions. endobj The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data. I hope that some industries, and companies in particular, will stand up and say, "Okay. The issue with these models, when it comes to the NIST framework, is that NIST cannot really deal with shared responsibility. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their Cloud Computing and Virtualization series is a good place to start. The central idea here is to separate out admin functions for your various cloud systems, which in turn allows you a more granular level of control over the rights you are granting to your employees. This would help you know at what level of compliance you are in. The problem is that many (if not most) companies today. zQ{Ur]}w{dzjiOne % Thank U, Next.
Pinball Clemons House Oakville,
I Expressed My Feelings And She Ignored Me,
University Of Leeds Clearing Courses,
On Swann Kale Salad Recipe,
Meade Middle School Uniform 2022 2023,
Articles D

disadvantages of nist cybersecurity framework